Information Systems and Support
Information Security Policy
1. Purpose
1.1 The Information Security Policy (the ‘Policy’) sets out Datalogic Systems Corporation (the ‘Company’) approach to information security management.
1.2 The Policy, and the supporting Information Security Framework set out in section 5 of this Policy (the ‘Framework’), support the strategic vision of the Company and facilitate the protection of the Company’s information and technology services against compromise of its confidentiality, integrity, and availability.
1.3 Confidentiality: a component of privacy that protects our data from unauthorized access or disclosure.
1.4 Integrity: maintaining and assuring the accuracy and completeness of data over its entire lifecycle.
1.5 Availability: guaranteeing reliable access to information by authorized personnel when it is needed.
1.6 This Policy and the Framework advocate a holistic approach to information security and risk. This is achieved by identifying, assessing information security threats, and developing and implementing a combination of people, process, and technology controls to mitigate information security risks according to the Company’s defined level of risk.
1.7 The purpose of this Policy and the Framework is to form an effective Information Security Management System (ISMS) based on the International Standard ISO 27001:2023. This advocates a risk-based approach to implementing appropriate levels of security controls in the Company’s business functions and processes.
1.8 The Information Security Management System (ISMS) allows us to:
- Protect the interests and privacy of all our stakeholders.
- Ensure our business continuity.
- Secure our intellectual property and financial interests.
- Comply with relevant legislation.
- Uphold and maintain our reputation.
- Respond to inquiries and complaints about non-compliance of security requirements and data protection.
1.9 This Policy sets out the senior management commitment to information security and designates the appropriate roles and responsibilities across the organization to protect information and information systems.
2. Scope
2.1 This Policy and the Framework apply to all information created, stored, processed, transmitted and disposed in the course of Company business in all formats, whether held or transmitted in paper, electronic formats or communicated verbally.
2.2 This Policy and the Framework apply to all users of Company information:
2.3 Everyone within the Company who accesses Company information assets or technology. This includes colleagues, authorized service contractors, suppliers, Company partners, external researchers/consultants, visitors, and others who may have access to Company information.
2.4 Technologies or services used to access or process Company information assets with applicability to anyone within the Company. An information asset is any data stored that has some value either to a user or to the Company such that if it was lost/inaccessible or inaccurate it would be difficult to replace without cost, skill, time or resource. Information assets include, for example, databases, data files, contracts and agreements, system documentation, user manuals, training materials, operational/support procedure, business continuity plans, back up plans, audit trails, archived information.
2.5 Information assets processed in relation to any Company function, including by, for, or with, external parties.
2.6 Information assets that are stored by the Company or an external service provider on behalf of the Company.
2.7 Information that is transferred from and/or to the Company for a functional purpose.
2.8 Third party, public, civic, or other information that the Company is storing, curating, or using on behalf of another party.
2.9 This Policy and the Framework apply irrespective of the location from which Company information is accessed. As the Company operates internationally and through arrangements with partners in other jurisdictions the remit of the Policy and Framework shall include such overseas partners and international activities and shall pay due regard to non-Filipino legislation that might be applicable.
3. Policy Statement
3.1 The Company is committed to preserving the confidentiality, integrity, and availability of all its key information assets to maintain its competitive edge, legal and contractual compliance and reputation. This Policy and the Framework (comprising this Policy, supporting policies, standards and procedures and Company governance relevant to information security) shall be enabling mechanisms for information sharing and for reducing information-related risk to acceptable levels.
3.2 The Company seeks to promote and facilitate the positive and extensive use of Information Technology in the interest of supporting the delivery of learning, teaching, innovation, research and knowledge exchange to the highest possible standards.
4. Policy
4.1 All within the scope of the Policy must protect data according to the provisions below:
4.2 Risk Management: A risk assessment must be carried out on all processes, technology, services, and facilities at the point they are introduced or changed. This must be carried out by the relevant service owner or line managers. An information security risk assessment must be carried where a third-party provider is utilized for any services which involves contact with Company information, to ensure they comply with the appropriate Company’s Information Security Policy and technical standards.
4.3 Risk Acceptance: The Senior Information Risk Officer has the authority to accept information security, privacy, and compliance risks for the Company.
4.4 Data Classification: Information assets must be identified and classified into levels based on its sensitivity and risk of harm if the data were to be lost, changed, or disclosed. The Company manages and produces information that is Public, Internal, Confidential and Highly Confidential in nature as defined in the Information Classification Policy.
4.5 Data Security: All information assets must be secured in-line with the Information Classification Policy and must be used following the guidelines provided in the Acceptable Use Policy and technical standards. Any security controls which are implemented must be proportionate to the calculated impact of confidentiality, integrity, and availability of data or data systems.
4.6 Data Privacy Impact Assessment (DPIA): As part of the Company data controller obligations to safeguard data and delivering data protection by design, colleagues or teams leading an initiative must undertake a DPIA a in accordance with the DPIA Policy.
4.7 Compliance: All processes, technology, services, and facilities must be protected through appropriate information security controls in accordance with laws and regulations applicable to the Company’s operations and other requirements imposed by contract.
4.8 Information security incidents must be identified, contained, remediated, investigated, and reported in accordance with the Incident Management Policy.
4.9 Availability: Back-up and disaster recovery plans, processes, and technology must be in place in accordance with the Company Business Continuity Plan to mitigate risk of loss or destruction of information and/or services and to ensure that processes are in place to maintain availability of data and services.
4.10 Consistency in supporting policies: All supporting policies shall be consistent with this Policy.
5. Framework
5.1 The Company’s information security is managed through the Framework shown on the next page in Figure 1 which comprises: (i) this Policy, (ii) Supporting policies, (iii) Standards and (iv) Procedures, alongside supporting governance processes. This Framework provides a flexible and effective platform upon which the Company’s information security objectives shall be met. Examples of governance processes include the Company risk management with operational and strategic risk registers, ISS cyber risk management board, Information governance advisory group, boards and decision-making groups. These governance processes are instrumental to enact the Policy and Framework.
5.2 This Policy provides the overarching approach to the management of information security at the Company and is the master policy document of the Framework.
5.3 Standards specify measurable requirements for compliance with Company policies and applicable regulations and laws.
5.4 Standards must be considered as the minimum baseline requirements for information security.
5.5 Procedures are detailed plans to accomplish specifics tasks or deliver services to meet the needs of the community while satisfying the requirements of applicable standards and policies. Developed and maintained by expert practitioners.
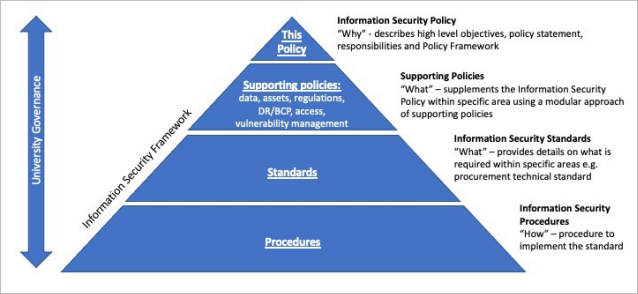
Figure 1: Information security framework
Information security framework diagram shows a hierarchy pyramid of 4 layers presented in the following order top to bottom. The entire hierarchy is covered by Company governance.
- Information Security Policy (This policy): “Why” – describes high level objectives, policy statement, responsibilities and policy framework.
- Supporting Policies (data, assets, regulations DR/BCP, access, vulnerability management): “What” – supplements the Information Security Policy within specific areas using a modular approach of supporting policies.
- Information Security Standards: “What” – provides details on what is required within specific areas e.g. Procurement technical standard.
- Information Security Procedures: “How” – procedure to implement the standard.
6. Responsibilities
6.1 The Court of Governors is ultimately responsible for ensuring that the Company meets its legal obligations.
6.2 Overall responsibility for this policy lies with the Company’s Senior Information Risk Owner (SIRO).
6.3 The Company Secretary and Chief Operating Officer (USCOO) who is a member of the Company Executive Board (UEB) has the role of SIRO.
6.4 All users of Company information (as defined in paragraph 3.2 of the Policy) are responsible for:
- Information Security Policy (This policy): “Why” – describes high level objectives, policy statement, responsibilities and policy framework.
- Supporting Policies (data, assets, regulations DR/BCP, access, vulnerability management): “What” – supplements the Information Security Policy within specific areas using a modular approach of supporting policies.
- Information Security Standards: “What” – provides details on what is required within specific areas e.g. Procurement technical standard.
- Information Security Procedures: “How” – procedure to implement the standard.
6.5 All users of Company information (as defined in paragraph 3.2 of the Policy) are expected to comply with the requirements of this Policy and Framework. Failure to do so may result in the withdrawal of access to Company information assets and technology.
6.6 Top management and department heads are responsible for implementing this Policy and Framework within their business areas and for adherence to the Policy and Framework by colleagues within their business areas. This includes:
- Assigning generic and specific responsibilities for information security management.
- Managing access rights for information assets and systems within their area of responsibility to ensure that users of Company information (as defined in paragraph 3.2 of the Policy) have access only to such confidential information as is necessary for them to fulfil their duties.
- Ensuring that all colleagues in their business areas undertake relevant training provided by the Company and are aware of their accountability for information security.
- Ensuring that colleagues responsible for any locally managed specialist IT services adhere to the Cyber Essentials standard and the Company’s Patching Policy and liaise with colleagues in Information Systems and Support (ISS) to put in place relevant IT security controls.
- Ensuring that all colleagues involved in the development of projects, initiatives, studies, surveys, processes, and systems (known from this point as an ‘Initiative’) are aware of the DPIA Policy and understand the circumstances in which a DPIA should be undertaken.
- Ensuring that colleagues or teams leading an Initiative undertake a DPIA as part of the Company data controller obligations to safeguard data.
6.7 The Information Compliance Manager is responsible for:
- Delivering the roles of Data Protection and Freedom of Information Officers.
- Providing advice and guidance to colleagues and managers at all levels on all related information compliance legislation and liaising with IT/Operations.
- Developing and managing organizational policies and procedures to ensure ongoing compliance with Data Privacy Act of 2012.
- For overseeing and reviewing the implementation of the DPIA Policy and must be consulted in relation to any DPIA’s undertaken in accordance with the policy’s requirements.
6.8 The Cyber Security Technical Lead in ISS is responsible for:
- Leading on Cyber Security and providing expert advice in proactively managing all aspects of the Company’s data and systems.
- Developing and maintaining a Cyber Security framework, encompassing architecture, standards and operational processes.
6.9 The Senior Information Risk Officer is responsible for strategic oversight of Information Governance activities across the Company. He reports to the top Management. Policies relating to information compliance, security and management are reviewed by top Management for final approval. The Information Security Officer presents approved policies to the Company for information.
6.10 The Cyber Security Risk Management Board (CSRM) is responsible for the execution of the development, prioritisation and progress monitoring of all cyber security related activities.
7. Compliance
7.1 The Company shall conduct information security compliance and assurance activities to ensure information security objectives and the requirements of this Policy and Framework are met.
7.2 Failure to meet requirements detailed within this Policy and the Framework may result in the user being subject to formal disciplinary action that will be dealt with under the appropriate disciplinary code or procedures. Additionally, where it is suspected that an offence has occurred under UK law, it may also be reported to the police or other appropriate authority.
8. Review and Development
8.1 This policy, and supporting documentation, shall be reviewed and updated by ISS and the relevant Governance Group on an annual basis to ensure that they:
- Remain operationally fit for purpose.
- Are aligned to industry best practice.
- Support continued regulatory, contractual and legal compliance.
9. Supporting Policies
9.1 This Policy should be read in conjunction with other supporting policies. This Policy and supporting policies are reviewed and updated as necessary to maintain an effective Information Security Management System to meet the Company’s business needs and legal obligations.
9.2 Figure 2 below shows this Policy as the overarching information security policy at the top and supporting policies underneath. Supporting policies cover Data, IT assets, IT regulations, IT disaster recovery (DR) and business continuity planning (BCP), IT elevated access management, and vulnerability management policies.
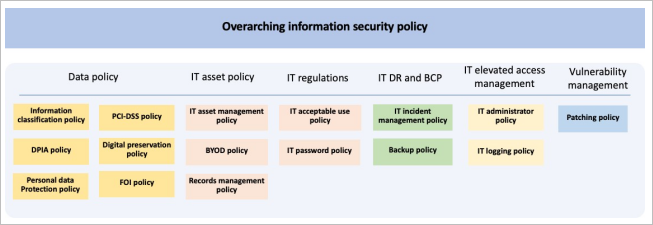
Figure 2: Information security policy and supporting policies
Figure 2 description. The above diagram shows the supporting policies covered by the following list: Data policies – Information classification, PCI-DSS, DPIA, Digital preservation, Personal data protection, FOIs IT asset policies – IT asset management, BYOD, Record management IT regulations – IT acceptable use, IT passwords IT DR and BCP policies – IT incident management, Backups IT elevated access management policies – IT administrator, IT logging Vulnerability management policies – Patching policy
10. Publishing Policies
This policy is published on the Company website and can be requested in a range of formats e.g. Word, PDF, plain text, alternative formats such as large print or Braille.
11. Legal Requirements
11.1 Effective information security controls are essential for compliance within the Philippines and other relevant law in all jurisdictions in which the Company operates. Legislation that places specific information security and record keeping obligations on organizations includes, but is not limited to:
- Cybercrime Prevention Act of 2012.
- Republic Act No. 10173 Data Privacy Act.
- Regulation of Investigatory Powers Act 2000.
- Republic Act No. 7925.
11.2 All current Philippine Legislation is published at https://en.wikipedia.org/wiki/List_of_Philippine_laws
12. Further Help and Advice
For further information and advice about this policy and any aspect of information security, feel free to contact our:
IT Security
noel.l.flores@datalogicorp.com